Page 473 - Invited Paper Session (IPS) - Volume 1
P. 473
IPS177 F. Ricciato et al.
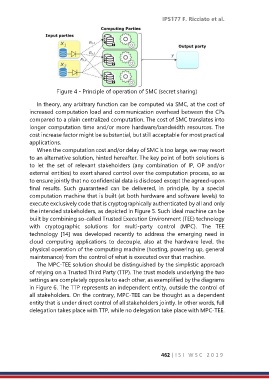
Figure 4 - Principle of operation of SMC (secret sharing)
In theory, any arbitrary function can be computed via SMC, at the cost of
increased computation load and communication overhead between the CPs
compared to a plain centralized computation. The cost of SMC translates into
longer computation time and/or more hardware/bandwidth resources. The
cost increase factor might be substantial, but still acceptable for most practical
applications.
When the computation cost and/or delay of SMC is too large, we may resort
to an alternative solution, hinted hereafter. The key point of both solutions is
to let the set of relevant stakeholders (any combination of IP, OP and/or
external entities) to exert shared control over the computation process, so as
to ensure jointly that no confidential data is disclosed except the agreed-upon
final results. Such guaranteed can be delivered, in principle, by a special
computation machine that is built (at both hardware and software levels) to
execute exclusively code that is cryptographically authenticated by all and only
the intended stakeholders, as depicted in Figure 5. Such ideal machine can be
built by combining so-called Trusted Execution Environment (TEE) technology
with cryptographic solutions for multi-party control (MPC). The TEE
technology [14] was developed recently to address the emerging need in
cloud computing applications to decouple, also at the hardware level, the
physical operation of the computing machine (hosting, powering up, general
maintenance) from the control of what is executed over that machine.
The MPC-TEE solution should be distinguished by the simplistic approach
of relying on a Trusted Third Party (TTP). The trust models underlying the two
settings are completely opposite to each other, as exemplified by the diagrams
in Figure 6. The TTP represents an independent entity, outside the control of
all stakeholders. On the contrary, MPC-TEE can be thought as a dependent
entity that is under direct control of all stakeholders jointly. In other words, full
delegation takes place with TTP, while no delegation take place with MPC-TEE.
462 | I S I W S C 2 0 1 9